The brand new PG_MEM malware targets PostgreSQL databases, exploiting weak passwords to ship payloads and mine cryptocurrency. Researchers warn that 800,000 publicly accessible situations are susceptible. Find out how this multi-stage assault works and the way to shield your PostgreSQL atmosphere.
Aqua Safety’s risk analysis staff, Nautilus, has found PG_MEM, a brand new malware that may infiltrate PostgreSQL databases, ship payloads, and mine cryptocurrency.
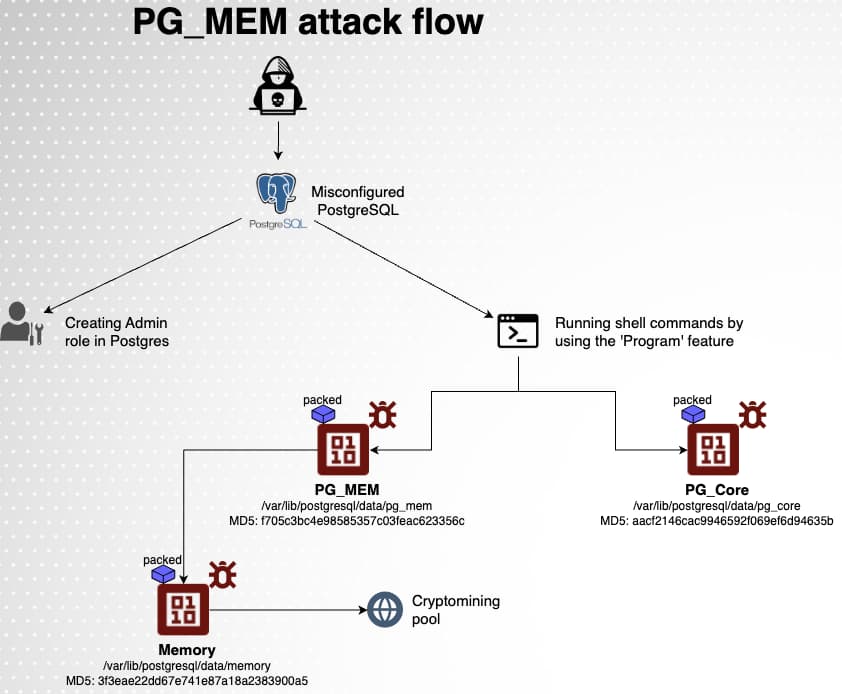
PostgreSQL, often known as Postgres, is an open-source relational database administration system researchers noticed as prone to brute pressure assaults. These assaults exploit weak passwords ensuing from misconfiguration or inadequate identification controls, a typical challenge in massive organizations.
This, in accordance to the corporate’s blog post, permits them to achieve entry to the database and execute arbitrary shell instructions by leveraging the COPY … FROM PROGRAM command, main to malicious actions like knowledge theft or malware deployment.
Nautilus researchers recognized 800,000 publicly accessible situations of PostgreSQL databases as susceptible to this malware. The last word purpose of the assault is to deploy cryptocurrency miners to exploit system sources.
The PG_MEM malware employs a multi-stage assault stream to compromise PostgreSQL databases and deploy cryptocurrency miners. It begins with the attacker initiating a brute pressure assault on the PostgreSQL database, repeatedly trying to guess the database credentials. As soon as this will get achieved, attackers create a brand new superuser function with excessive privileges. This permits them to keep entry to the database even when the unique credentials are modified.
Now, the attacker gathers details about the system, such because the PostgreSQL server model and configuration to establish potential vulnerabilities and tailor the assault accordingly. The attacker downloads malicious payloads from a distant server, which usually contains cryptocurrency mining software program and instruments for persistence and evasion.
Researchers famous that two information are downloaded from the attacker’s distant server, with the primary block of instructions geared toward delivering the primary payload. They used a brief desk to retailer code and knowledge, clearing it earlier than and after every command. As quickly because the payloads are downloaded on the compromised system, the cryptocurrency mining software program begins to eat system sources to mine cryptocurrency.
The attacker takes steps to guarantee persistence, reminiscent of creating cron jobs or modifying system configuration information, which helps the malware to proceed working even after the system is restarted. Furthermore, they evade detection by deleting information and logs associated to their malicious exercise.
That is regarding as PostgreSQL databases are generally used for net, cell, geospatial, and analytics functions. To guard PostgreSQL environments, organizations ought to monitor for suspicious exercise, implement robust authentication utilizing strong passwords and multi-factor authentication, isolate databases from the community, and use safety instruments to promptly detect and forestall malicious exercise.