Microsoft and Cloudflare have disrupted a Phishing-as-a-Service operation promoting the RaccoonO365 equipment for stealing Microsoft 365 account credentials.
“Utilizing a courtroom order granted by the Southern District of New York, [we] seized 338 web sites related to the fashionable service, disrupting the operation’s technical infrastructure and chopping off criminals’ entry to victims,” announced Steven Masada, Assistant Normal Counsel at Microsoft’s Digital Crimes Unit (DCU).
Who’s behind RaccoonO365?
RaccoonO365 (aka Storm-2246) bought pre-packaged, subscription-based phishing kits, which allowed low-skilled attackers to ship out emails impersonating trusted manufacturers like DocuSign, SharePoint, Adobe, and Maersk and arrange pretend, Microsoft-branded login pages to seize authentication credentials and cookies.
“When the sufferer enters their credentials, the equipment acts as an adversary-in-the-middle, proxying the authentication stream to Microsoft’s servers and permitting the attacker to seize not solely the password but additionally the ensuing session cookie, successfully bypassing MFA,” Cloudflare famous.
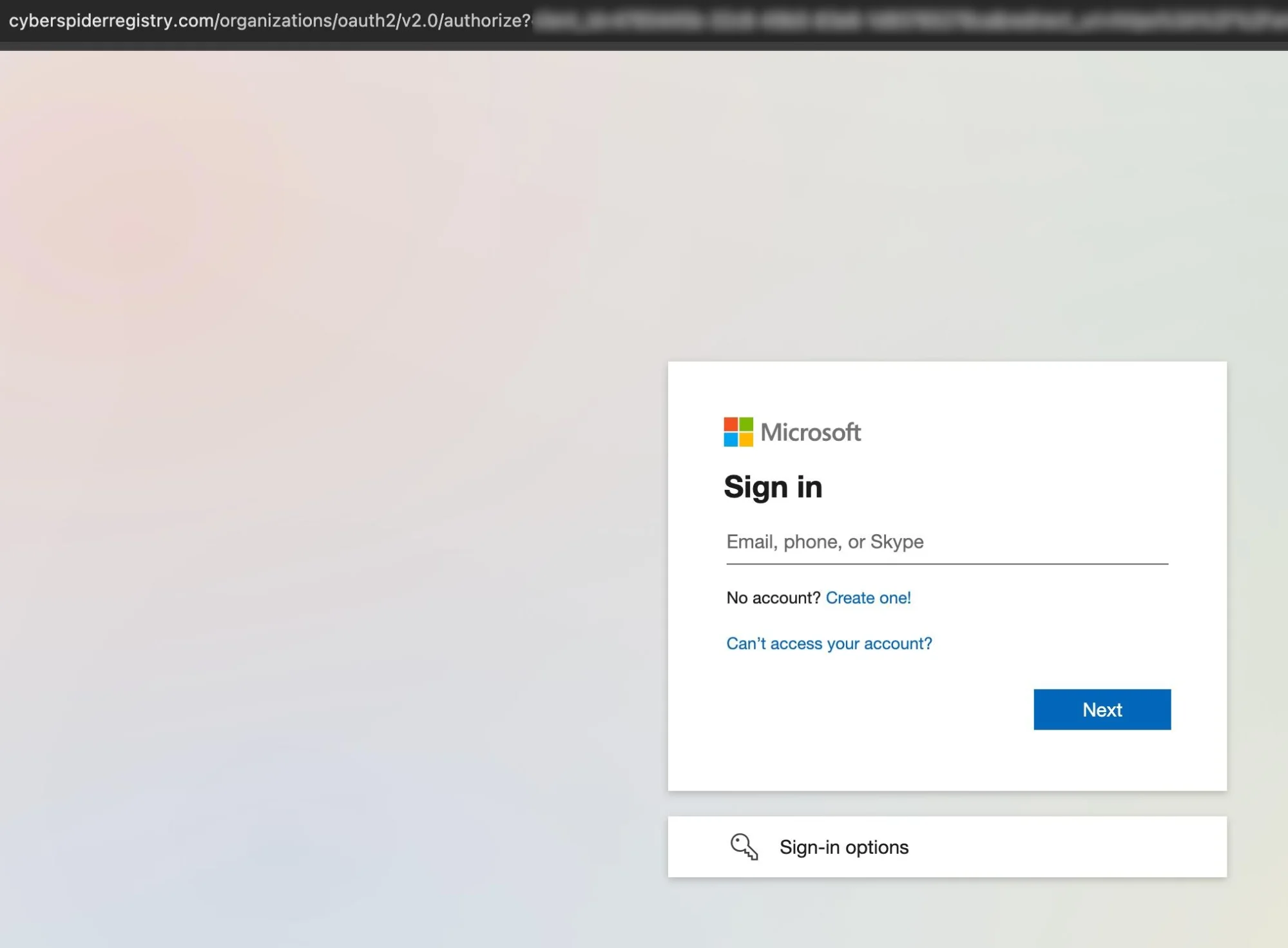
A phishing web page arrange by a RaccoonO365 buyer (Supply: Cloudflare)
Microsoft secretly bought the phishing kits and the directions from the group, and this allowed them to trace the cryptocurrency transactions of the group.
An operational safety lapse by the risk actors – specifically, their inadvertent disclosure of a secret cryptocurrency pockets – helped Microsoft perceive the group’s operations and, finally, put a reputation to the RaccoonO365 group’s leader: Joshua Ogundipe.
The Nigeria-based man, alongside along with his associates, makes use of Telegram to market the service/software through a non-public channel.
“Based mostly on Microsoft’s evaluation, Ogundipe has a background in pc programming and is believed to have authored the majority of the code.”
Two of the different defendants present administrative and technical assist and assist promote the service, whereas the different two are cybercriminals who bought the Raccoom0365 phishing equipment, registered a brand new phishing domains, and included it into the group’s technical infrastructure.
In August, Microsoft filed a lawsuit in opposition to Ogundipe and 4 unnamed associates, who stay at massive.
What’s subsequent?
Cloudflare says that the RaccoonO365 platform operates on a tiered pricing mannequin with choices structured to enchantment to a variety of criminals.
“Plans are bought in numerous durations, reminiscent of a 30-day plan for $355 and a 90-day plan for $999. The service completely accepts cryptocurrencies, together with USDT (TRC20, BEP20, Polygon) and Bitcoin (BTC),” the firm defined.
Up to now, the group has “earned” a minimum of $100,000 by their felony enterprise, and continues evolving its providing. The newest marketed addition is RaccoonO365 AI-MailCheck, designed to scale operations and improve the effectiveness of assaults.
“A felony referral for Ogundipe has been despatched to worldwide regulation enforcement,” Masada added, and famous that submitting a lawsuit is simply the begin.
“We all the time anticipate actors to attempt to rebuild their operations. Which means the DCU will proceed to take extra authorized steps in the case to dismantle any new or reemerging infrastructure,” he famous.

Subscribe to our breaking information e-mail alert to by no means miss out on the newest breaches, vulnerabilities and cybersecurity threats. Subscribe here!















