A lately found cross-platform malware, appropriately named JaskaGO, has surfaced, focusing on each macOS and Windows methods.
Cybersecurity researchers at AT&T Alien Labs have found a classy malware pressure known as JaskaGO, crafted within the Go (Golang) programming language and geared up with the power to take care of persistence in contaminated methods. It might probably exfiltrate priceless info, together with browser credentials and cryptocurrency pockets particulars.
JaskaGO was detected in July 2023, focusing on Mac customers. Since then, the risk has developed its capabilities and developed in each macOS and Windows variations, with a low detection fee, as evidenced by latest anti-virus engine samples.
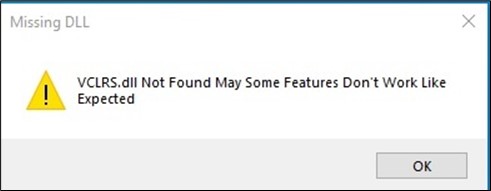
Based on AT&T Alien Labs’ report, JaskaGO is a misleading device that presents a faux error message claiming a lacking file to mislead customers into believing the malicious code did not run.
Additional, it makes use of file names resembling well-known purposes, similar to “Capcut_Installer_Intel_M1.dmg” and “Anyconnect.exe,” suggesting a standard technique of malware deployment below the guise of reputable software program in pirated utility internet pages.
The malware first scans the system to find out whether it is working inside a digital machine (VM), acquiring normal machine info, such because the variety of processors, system up-time, obtainable system reminiscence, and MAC addresses. The presence of MAC addresses related to well-known VM software program, similar to VMware or VirtualBox, is a key indicator.
If not detected, it begins gathering info and repeatedly queries its C2 server, awaiting directions for numerous instructions. These instructions embody creating persistence, stealer functionalities, pinging the command and management, executing shell instructions, alert messages, retrieving the working course of listing, executing information on disk or in reminiscence, writing to the clipboard, performing random duties, downloading and executing extra payloads, initiating the method to exit (self), and initiating the method to exit and delete itself.
JaskaGO is provided with intensive knowledge exfiltration capabilities, and shops acquired knowledge in a specifically created folder, zipping and sending it to the attacker. It may be configured to focus on extra browsers, gathering browser info similar to credentials, historical past, cookies, password encryption keys, profile information, and login info.
Persistence mechanisms are established by means of two strategies: Service Creation in Windows and Execution as Root in macOS. In Windows, the malware creates a Windows Terminal profile by producing the file: UserNameAppDataLocalPackagesMicrosoft. WindowsTerminal_*LocalStatesettings.json.”
On macOS, the malware employs a multi-step course of to determine persistence inside the system: Execution as Root, Disabling Gatekeeper, and Duplicating itself. To make sure persistence, the malware creates both LaunchDaemon or LaunchAgent based mostly on profitable root entry to get routinely launched throughout system startup and additional embed itself into the macOS surroundings.
JaskaGO remains to be being investigated; however serves as a warning to Mac customers who could have felt unaffected by cyber threats, emphasizing the significance of fixed vigilance whatever the chosen working system.
RELATED ARTICLES
- BlueNoroff APT Targeting macOS with ObjCShellz Malware
- Lazarus Group uses KandyKorn macOS malware for crypto theft
- Cracked macOS Software Laced with New Trojan Proxy Malware
- New Malware Turns Windows and macOS Devices into Proxy Nodes
- Researchers Leverage ChatGPT to Expose Notorious macOS Malware
- Windows, Linux, macOS Users Targeted by Chinese Iron Tiger APT Group
New JaskaGO Malware Targets Mac and Windows for Crypto, Browser Data www.hackread.com 2023-12-20 22:34:15
Source link