Google’s Menace Intelligence Group (GTIG) has uncovered that North Korean risk actor UNC5342 is weaponizing EtherHiding, a novel malware supply approach leveraging public blockchains, to conduct massive‑scale cryptocurrency theft.
This marks the primary identified occasion of a nation‑state actor adopting the EtherHiding approach, beforehand linked to financially motivated teams like UNC5142.
Exploiting the Blockchain for Persistence
EtherHiding first emerged in 2023 as a part of the CLEARFAKE marketing campaign. It entails embedding malicious JavaScript payloads immediately into blockchain good contracts, significantly on the BNB Good Chain and Ethereum networks, remodeling decentralized ledgers into resilient, takedown‑proof command‑and‑management servers.
In UNC5342’s operations, the hackers use social engineering below the marketing campaign title “Contagious Interview,” which impersonates recruiting processes at crypto and tech companies.
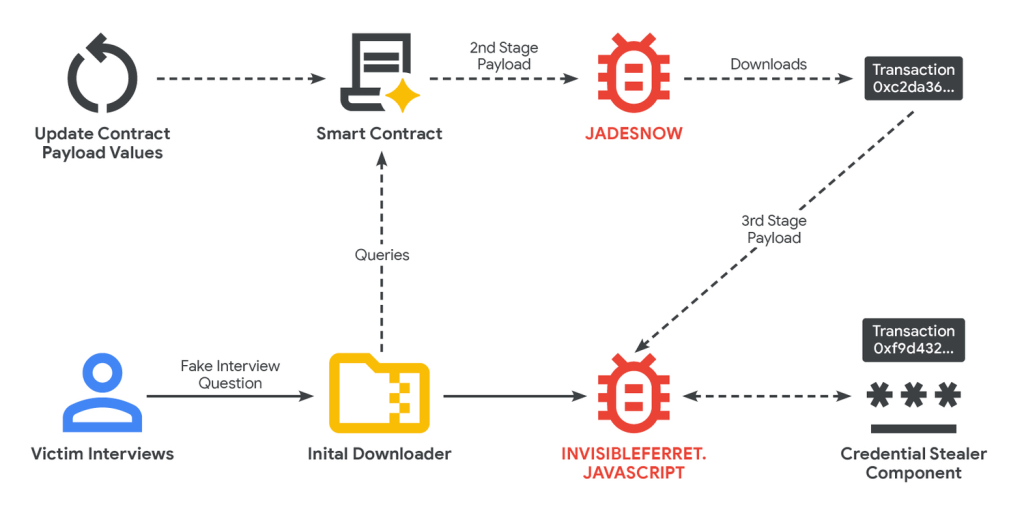
Victims are lured with faux job interviews or coding exams that ship the JADESNOW downloader malware, which then makes use of EtherHiding to fetch and execute the subsequent‑stage payload INVISIBLEFERRET.
GTIG’s analysis exhibits the loader retrieves malicious knowledge from blockchain transactions by way of learn‑solely eth_call The request is for a stealthy mechanism that avoids gasoline charges and leaves no traceable transaction report.
The actors regularly replace their malicious good contracts, every revision costing lower than $2 in gasoline charges, enabling speedy reconfiguration of payload supply.
Multi‑Stage Assault Chain and On‑Chain Operations
The an infection chain begins when victims obtain malicious JavaScript or npm packages through the faux technical evaluation section. JADESNOW, written in JavaScript, communicates with good contracts corresponding to 0x8eac3198dd72f3e07108c4c7cff43108ad48a71c on the BNB Good Chain.
The contract’s encoded and XOR‑encrypted payload spawns the subsequent stage, INVISIBLEFERRET, which is deployed in reminiscence to set up a distant backdoor.
Telemetry reveals INVISIBLEFERRET connects to attacker‑managed MySQL servers on port 3306, exfiltrating system knowledge and storing stolen credentials, session cookies, and pockets data in ZIP archives uploaded to distant servers and personal Telegram chats.
UNC5342’s use of a number of blockchain networks demonstrates subtle operational compartmentalization, switching payload internet hosting between BNB Good Chain and Ethereum for value and evasion benefits.
GTIG emphasizes that each UNC5342 and UNC5142 depend on centralized API providers, corresponding to Binplorer or Ethplorer, reasonably than direct blockchain node interplay.
This dependency introduces restricted mitigation alternatives for safety groups to establish and block malicious API visitors, regardless that the blockchain knowledge itself stays immutable.
The campaign underscores a rising development of state‑sponsored actors abusing decentralized infrastructure to obtain persistence, anonymity, and management.
In accordance to GTIG, EtherHiding represents a brand new frontier in “bulletproof” malware internet hosting, solidifying the convergence of Web3 applied sciences and nation‑state cybercrime.
Discover this Story Attention-grabbing! Comply with us on Google News , LinkedIn and X to Get Extra Immediate Updates














