Safety researchers have uncovered a complicated provide chain assault disguised as a authentic cryptocurrency pockets.
Socket’s Risk Analysis Staff discovered a malicious Chrome extension referred to as “Safery: Ethereum Wallet,” printed on the Chrome Internet Retailer on November 12, 2024, that employs an ingenious method to steal person seed phrases via hidden blockchain transactions.
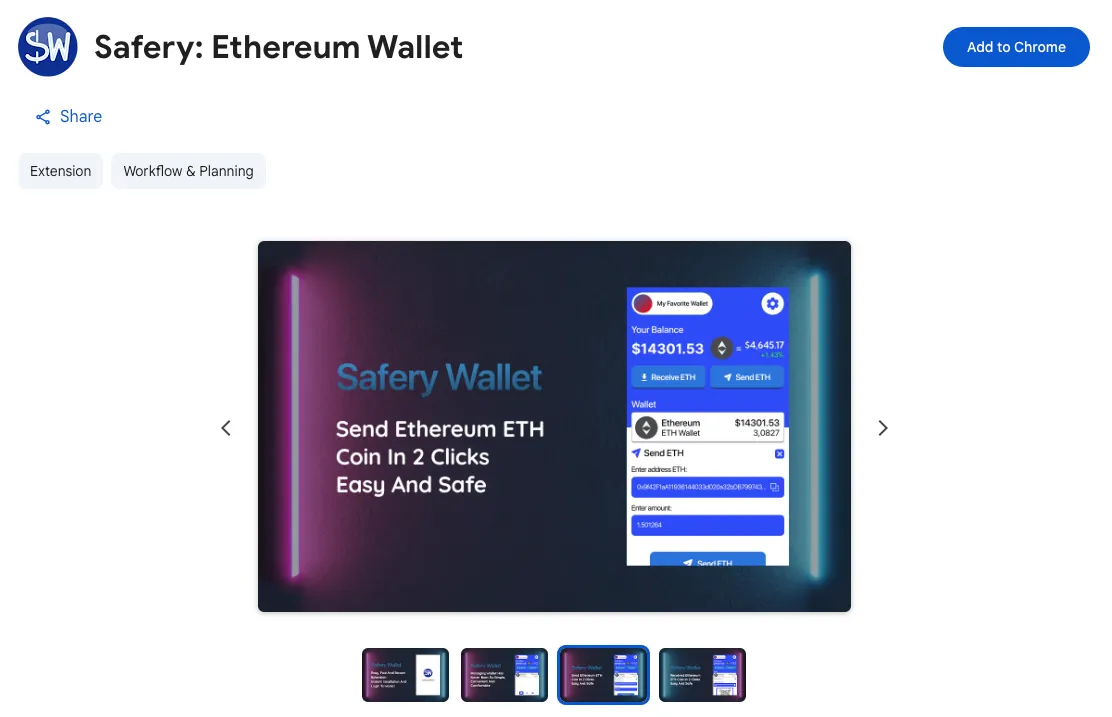
The extension, recognized by its ID fibemlnkopkeenmmgcfohhcdbkhgbolo, markets itself as a safe and simple Ethereum pockets providing fast two-click transfers and simple stability administration.
Nonetheless, beneath this benign exterior lies a complicated backdoor that exfiltrates seed phrases by encoding them into Sui blockchain addresses and broadcasting microtransactions from a menace actor-controlled pockets.
When customers create or import a pockets, the malicious extension encodes their BIP-39 mnemonic into one or two artificial Sui-style addresses.
The extension then sends 0.000001 SUI to those encoded addresses utilizing a hardcoded menace actor mnemonic. By decoding the transaction recipients, the attacker reconstructs the unique seed phrase with out requiring conventional command-and-control infrastructure.
This method hides exfiltration inside legitimate-looking blockchain transactions which can be almost not possible to detect via standard monitoring.
The extension’s technical implementation is subtle. It masses the usual BIP-39 wordlist, maps every phrase to its numeric index, and packs these indices right into a hexadecimal string prefixed with “0x” to resemble a legitimate Sui deal with.
The malware by no means shows Sui balances or prompts for Sui actions these capabilities exist solely to remodel seed phrases into blockchain-compatible information showing innocuous to exterior observers.
Misleading Distribution
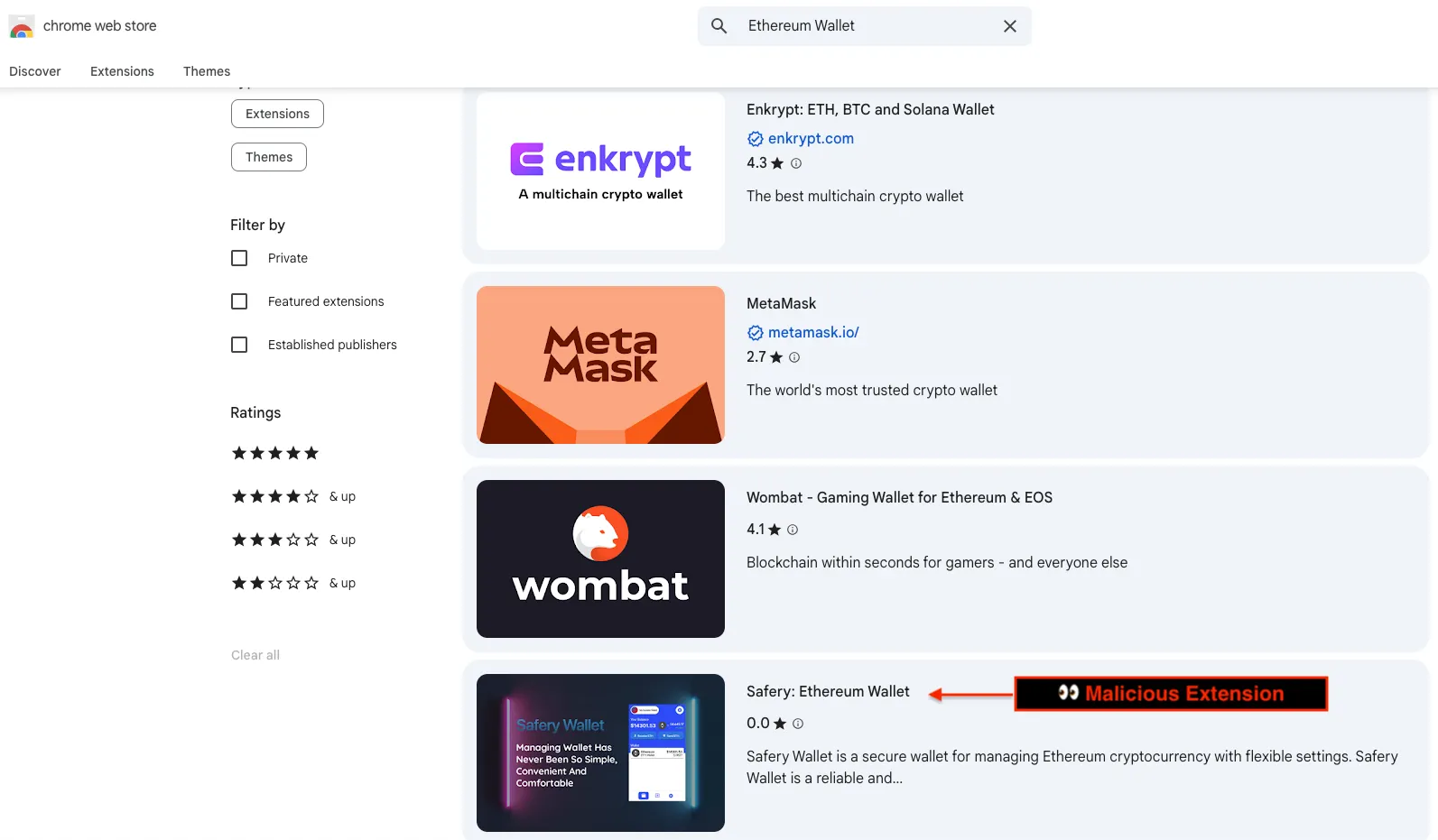
The extension’s misleading look amplifies its menace. When looking out “Ethereum Wallet” on the Chrome Internet Retailer, Safery seems because the fourth consequence, positioned alongside authentic wallets like MetaMask and Enkrypt.
SaferyThe developer’s privateness disclosure falsely claims no person information assortment and that non-public keys stay on the machine assurances that straight contradict the extension’s precise performance.
The assault chain is seamless. When customers enter a legitimate seed phrase throughout login or pockets creation, the extension encodes it into artificial Sui addresses and broadcasts microtransactions from the hardcoded menace actor pockets.
Promotional photographs promise “Simple, Quick And Safe Extension” and “Ship Ethereum ETH Coin In 2 Clicks Simple And Protected”.
Safery.This distinguished placement provides the malicious extension a right away veneer of legitimacy to unsuspecting customers, considerably rising set up charges earlier than safety assessment or takedown happens.
The Chrome Internet Retailer itemizing guarantees “Simple, Quick And Safe Extension” with reliability, privateness, and easy stability administration.
Every transaction recipient deal with encodes the sufferer’s full mnemonic. Utilizing the embedded decoder, the menace actor reconstructs the seed phrase phrase by phrase with none central C2 server or plaintext HTTP transmission.
With the recovered mnemonic, attackers acquire full management of all derived wallets and may drain property to their addresses. The seed by no means travels in plaintext over HTTP, making detection terribly troublesome.
Response and Suggestions
At reporting time, the extension remained reside on the Chrome Internet Retailer. Socket submitted a takedown request to Google Chrome Internet Retailer safety staff, requesting suspension of the writer account.
The extension’s Socket AI Scanner evaluation flagged recognized malware standing, elevated Chrome permissions, dynamic code execution, and outbound community entry.
Defenders ought to deal with surprising blockchain RPC calls from the browser as high-risk indicators, implement Chrome Enterprise allowlists, and prohibit installs to authorised extension IDs.
Customers ought to set up wallets completely from verified writer pages and like established choices like MetaMask or Phantom with confirmed safety observe data.
This incident demonstrates that seed phrase theft may be hid completely inside public blockchain site visitors, making conventional detection strategies ineffective.
Comply with us on Google News, LinkedIn, and X to Get On the spot Updates and Set GBH as a Most popular Supply in Google.













